Blocking iOS third-party marketplaces and web distribution in the EU
Apple released with iOS 17.4 and iOS 17.5 with two minor updates for users in the European Union to comply with the EU’s Digital Markets Act new features. In these releases users located in the EU have the possiblity to install 3rd party App Stores (aka Marketplaces in 17.4) and to download iOS apps directly from websites (aka Web Distribution in 17.5). If you wanna block users to install these on managed, corporate devices you can find here how.
What does this mean?
You can find a very detailed description what was changed in this Apple support document.
New for enterprise admins
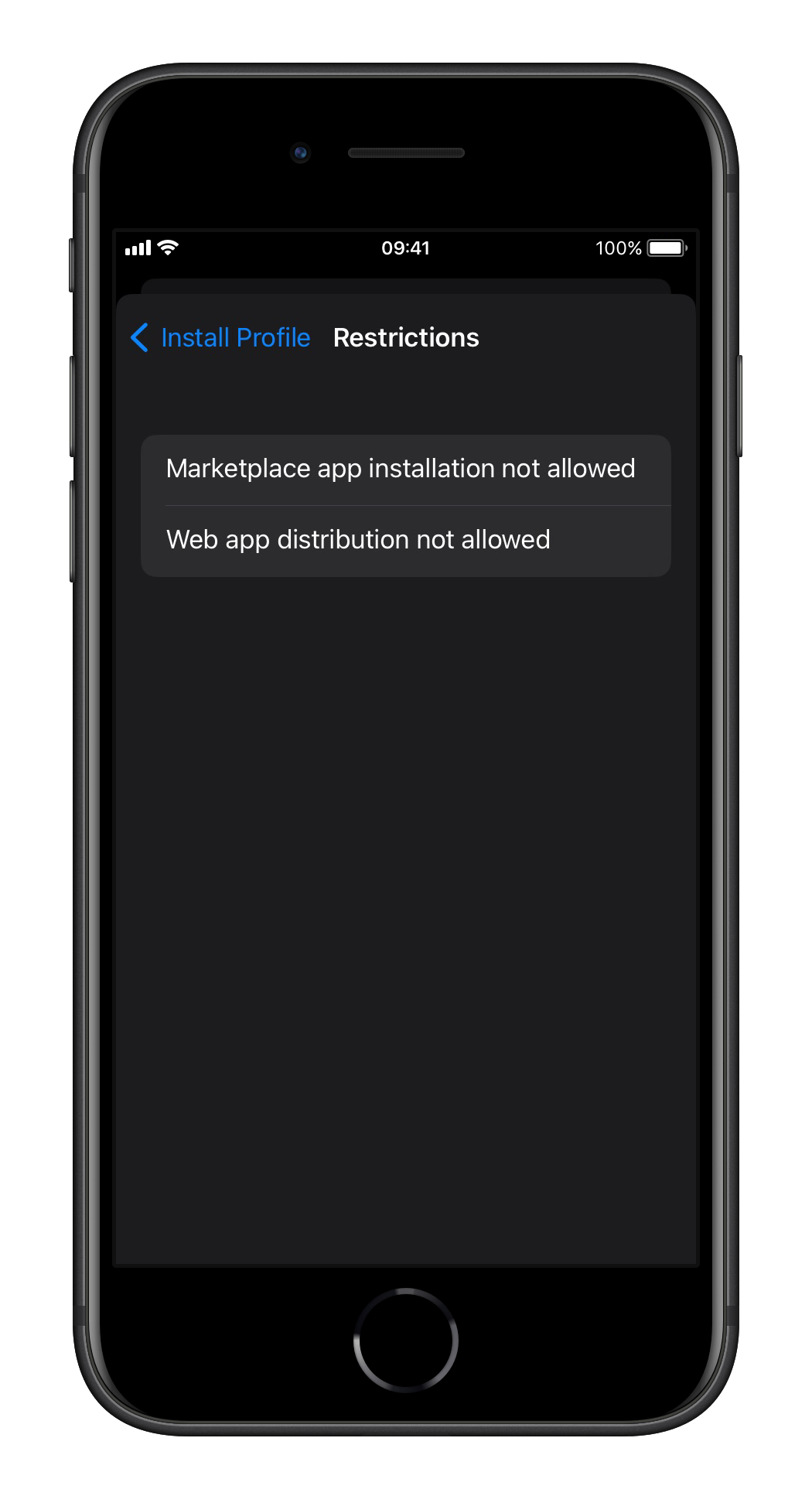
In case you want to block one or both new distribution methods of apps you can do this quiet easy with two new device restrictions that are supported on supervised devices.
- allowMarketplaceAppInstallation - iOS 17.4 includes a new Restriction key to prevent installing third-party app marketplaces on supervised iPhones in the EU.
- allowWebDistributionAppInstallation - iOS 17.5 includes a new Restriction key allowWebDistributionAppInstallation to prevent installing apps through Web Distribution on supervised iPhones in the EU.
These already known restriction keys were updated to apply as well to the new distribution methods above:
- allowAppInstallation
- allowAppRemoval
- allowListedAppBundleIDs
- blockAppBundleIDs
The unexpected problem
What I mentioned during testing and deployment of the new settings as custom profiles via Microsoft Intune is that you have to be a little careful. This is because you can deploy this settings to all your devices and the profile reporting looks nice and clean. This is not working as you would expect on your devices. If you assign this configurations to iOS devices before 17.4 (allowMarketplaceAppInstallation) or before 17.5 (allowWebDistributionAppInstallation) is installed the report shows a successful deployment but the restriction does not apply (does not show in the management profile locally) and is not re-applied after the OS update is installed.
To overcome this (IMHO implementation flaw in iOS restrictions that is not taken in account by Intune) you can create to assignment filters that look like this.
Warning: You have to maintain them with upcoming iOS releases. I just added a few minor and patch versions in advance that may not be released ever to be prepared.
Go to Intune admin center -> Tenant administration -> Filters and create two new filters for the Platform ‘iOS/iPadOS’. I used in this example rule syntax a combination of the ‘device.enrollmentProfileName’ to target only supervised devices and a ‘device.osVersion’ list of ‘17.4 to 17.6.3’ and ‘17.5 to 17.6.3’ respectively. Edit: You can after the 2408 Intune release use -ge, -gt, -le and -lt operators in preview. This simplifies the filters. I added the simplified filters below
Filter name: iOS 17.4+
((device.enrollmentProfileName -eq "YourEnrollmentProfileName") and
(device.osVersion -in
["17.4","17.4.1","17.4.2","17.4.3","17.5","17.5.1","17.5.2","17.5.3","17.6","17.6.1","17.6.2","17.6.3"])
Filter name: Simplified iOS 17.4+
((device.enrollmentProfileName -eq "YourEnrollmentProfileName") and
(device.osVersion -ge "17.4")
Filter name: iOS 17.5+
((device.enrollmentProfileName -eq "YourEnrollmentProfileName")
and (device.osVersion -in
["17.5","17.5.1","17.5.2","17.5.3","17.6","17.6.1","17.6.2","17.6.3"])
Filter name: Simplified iOS 17.5+
((device.enrollmentProfileName -eq "YourEnrollmentProfileName")and (device.osVersion -ge "17.5")
Now you can simply add this filters to the respective custom profiles and you will not see this unintended behavior.
Edit: Martijn van Loenhout mentioned that allowMarketplaceAppInstallation is now (Service release 2403) already available as Setting Catalog configuration in Intune. You can use this for sure as well if you prefer this.
applefreakz-allowmarketplaceappinstallation-false.mobileconfig:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadDisplayName</key>
<string>Restrictions</string>
<key>PayloadIdentifier</key>
<string>com.apple.applicationaccess.24BB5BE8-DCB8-4876-9F16-7C6D25CABF78</string>
<key>PayloadType</key>
<string>com.apple.applicationaccess</string>
<key>PayloadUUID</key>
<string>24BB5BE8-DCB8-4876-9F16-7C6D25CABF78</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>allowMarketplaceAppInstallation</key>
<false/>
</dict>
</array>
<key>PayloadDescription</key>
<string>Block third-party app marketplaces</string>
<key>PayloadDisplayName</key>
<string>applefreakz_allowMarketplaceAppInstallation-FALSE</string>
<key>PayloadIdentifier</key>
<string>de.applefreakz.987A43C8-F8E8-4636-8C82-9FDAD46AB686</string>
<key>PayloadOrganization</key>
<string>applefreakz</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>CDC18090-077D-48BF-9621-86ECFAA3C327</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>
applefreakz-allowwebdistributionappinstallation-false.mobileconfig
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>PayloadContent</key>
<array>
<dict>
<key>PayloadDisplayName</key>
<string>Restrictions</string>
<key>PayloadIdentifier</key>
<string>com.apple.applicationaccess.BFB998BC-3E8B-4252-816E-A6795D302D34</string>
<key>PayloadType</key>
<string>com.apple.applicationaccess</string>
<key>PayloadUUID</key>
<string>BFB998BC-3E8B-4252-816E-A6795D302D34</string>
<key>PayloadVersion</key>
<integer>1</integer>
<key>allowWebDistributionAppInstallation</key>
<false/>
</dict>
</array>
<key>PayloadDescription</key>
<string>Block app installation through Web Distribution</string>
<key>PayloadDisplayName</key>
<string>applefreakz_allowWebDistributionAppInstallation-FALSE</string>
<key>PayloadIdentifier</key>
<string>de.applefreakz.8AE1F450-602E-4156-B149-CE1E9CD0F469</string>
<key>PayloadOrganization</key>
<string>applefreakz</string>
<key>PayloadType</key>
<string>Configuration</string>
<key>PayloadUUID</key>
<string>E5A4DE5C-E468-40A9-B4C4-D2D2D063E3DE</string>
<key>PayloadVersion</key>
<integer>1</integer>
</dict>
</plist>
In the management profile you will see two new restrictions like this: